NETWORK PROTECTION
BGP-based mitigation of DDoS attack consequences
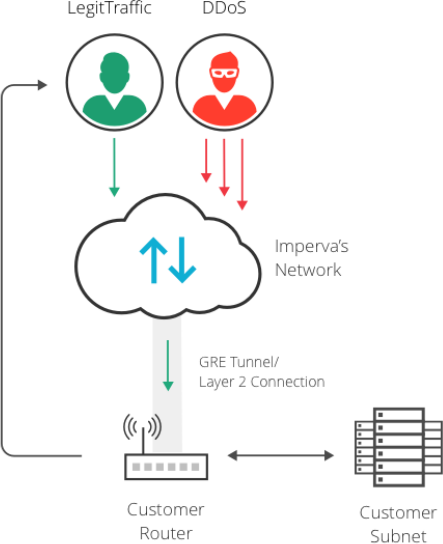
Our DDoS attack protection defends entire networks by leveraging multi-terabit throughput of Imperva’s network and capability to process packets with high efficiency to immediately mitigate effects of the largest and most sophisticated DDoS attacks.
Imperva supports multiple deployment models, including Cross Connect, GRE tunnels and Equinix Cloud Exchange. Network protection is available in two variants: always-on and on-demand. In the latter case, the service is implemented with a flow-based monitoring function and support for automatic or manual switching.
Immediate interception of attacks of any scale
Imperva's global network is capable of on-demand cleaning of more than 6 terabits of traffic per second and is able to process 65 billion attack packets per second. Upon activation, the service blocks any attack in less than 3 seconds. The typical time of attack mitigation is 1 second.
Minimal delays
Our network of data centers allows for transfer times of less than 50 milliseconds to over 90% of countries around the world. This ensures that your server operates smoothly even when under attack.
Flexible activation
DDoS protection for networks is available as an always-on or on-demand service with support for automatic or manual switching.
Protection for resources in cloud environments
DDoS protection for networks defends any resources in network layers, including AWS, Azure and Google Cloud whether they are hosted, private, or public cloud environments.
Direct protection (optional)
Direct connection of layer 2 with Imperva's scrubbing centers is available for deployments with uninterrupted operation or environments that are very sensitive to latency.
Support for all device types
DDoS protection for network supports any type of service, including TCP, UDP, SMTP, FTP, SSH, VoIP and proprietary or custom protocols.
Visibility of attacks
Dashboards that are being kept up to date allow for monitoring traffic related to attacks, including vector types, PoP traffic and IP coverage statistics.